I just had a hard time figuring out that a network routing setup was not working due to a correctly enforced IP Spoofing protection on a Palo Alto Networks firewall. Why was it a hard time? Because I did not catch that the IP spoofing protection kicked in since there were no logs. And since we do log *everything*, a non-existent log means nothing happened, right? Uhm, not in this case. Luckily you can (SHOULD!) enable an additional thread log on the Palo.
The exception proves the rule. That is: blocks/drops that are enforced with these options are NOT logged in any way within the GUI:
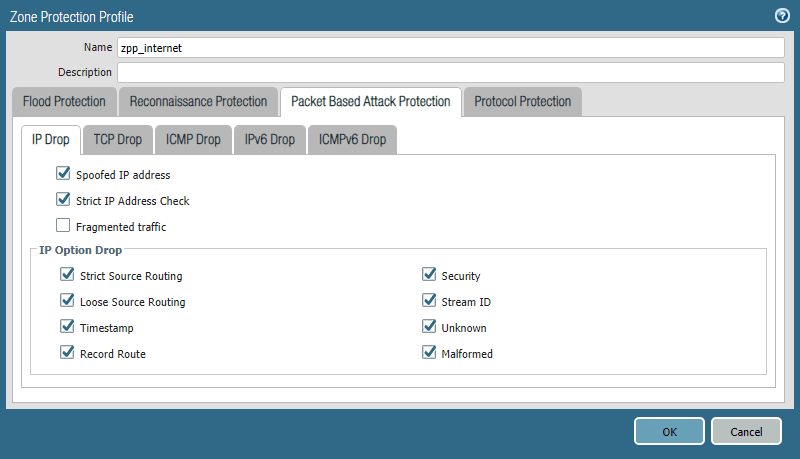
The only way to find some drops, e.g., spoofed IP addresses (aka unicast reverse path forwarding), was the global counters along with an appropriate packet filter (from the GUI at Monitor -> Packet Capture):
weberjoh@pa(active)> show counter global filter packet-filter yes | match spoof flow_dos_pf_ipspoof 1908 0 drop flow dos Packets dropped: Zone protection option 'discard-ip-spoof'
Investigating IP Drops (amongst others)
With PAN-OS 8.1.2, Palo Alto Networks released a new feature: “Logging of Packet-Based Attack Protection Events“. With this feature, all (?) protections are logged in the threat log which is accessible through the GUI.
set system setting additional-threat-log onSome notes about this CLI command:
- it does not require a reboot -> it is live instantly
- it is persistent, that is: it survives a reboot of the firewall
- it is NOT part of the configuration file -> if you’re doing an RMA or a tech refresh you have to set it again!
- it is NOT synced within an HA cluster -> you have to enable it on every single firewall
- you can verify whether or not this logging feature is enabled with the following command: show system state filter cfg.general.additional-threat-log
However, please enable it carefully to not overwhelm your logs. ;)
This is how I’ve done it on one of my firewalls. Checked it, enabled it, checked it again:
weberjoh@pa(passive)> show system state filter cfg.general.additional-threat-log 'cfg.general.additional-threat-log': NO_MATCHES weberjoh@pa(passive)> weberjoh@pa(passive)> weberjoh@pa(passive)> set system setting additional-threat-log on weberjoh@pa(passive)> weberjoh@pa(passive)> weberjoh@pa(passive)> show system state filter cfg.general.additional-threat-log cfg.general.additional-threat-log: True weberjoh@pa(passive)>
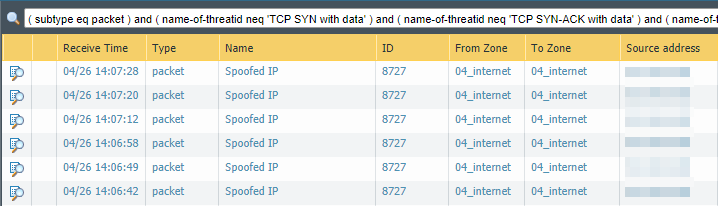
And this is what the protection against IP spoofs looks like in the threat log:
By the way: Google pointed me to the solution on Reddit respectively Palo Altos LIVEcommunity. Meanwhile, I was confused by a new feature from PAN in a non .0 PAN-OS version. Anyway, some more feature requests to Palo Alto Networks:
- Feature request #1: enabling/disabling this feature through the GUI just like any other feature.
- Feature request #2: adding a big sign at the zone protection profile about these probably not logged blocks.
Photo by Lucas Alexander on Unsplash.