More than 6 years ago (!) I published a tutorial on how to set up an IPsec VPN tunnel between a Palo Alto Networks firewall and a Cisco ASA. As time flies by, ASA is now able to terminate route-based VPN tunnels (which is great!), we have IKEv2 running everywhere and enhanced security proposals. Hence, it’s time for an update:
My Setup
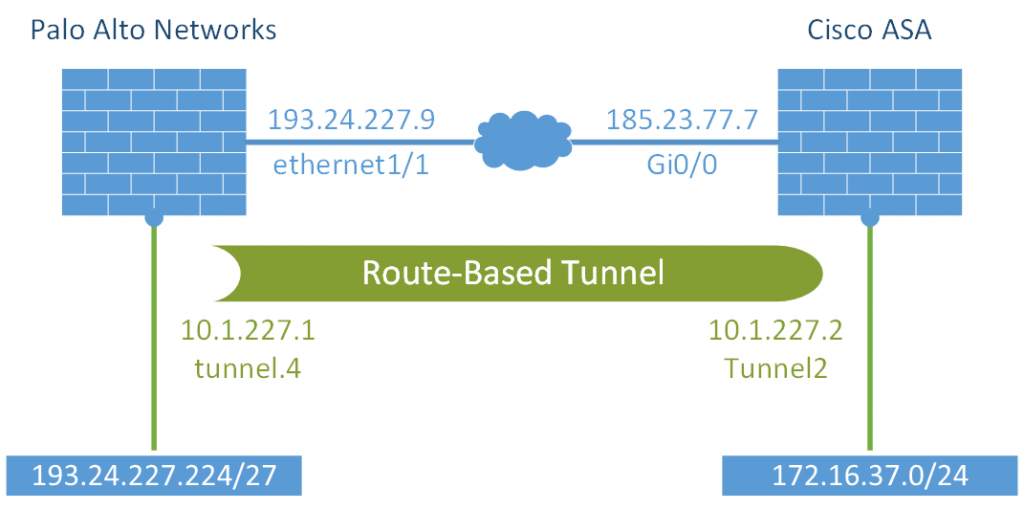
This is my setup for this tutorial: (Yes, public IPv4 addresses behind the Palo.)
I am using a Palo Alto Networks PA-220 with PAN-OS 10.0.2 and a Cisco ASA 5515 with version 9.12(3)12 and ASDM 7.14(1). These are the VPN parameters:
- Route-based VPN, that is: numbered tunnel interface and real route entries for the network(s) to the other side. But no proxy-IDs aka traffic selection aka crypto map. Thank goodness for that.
- IKEv2 (no distinction anymore between main or aggressive mode as with IKEv1)
- PSK: 30 chars alphanumeric, generated with a password generator! (ref)
- IKE crypto/policies:
- Diffie-Hellman group 20
- AES-256-CBC (because Palo has no -GCM here, don’t know why)
- SHA-512 (you could use SHA-256 if you like)
- 8 hours
- IPsec crypto/proposals/transform sets:
- AES-256-GCM (here it is GCM)
- SHA-512 (again, you can use SHA-256 as well)
- Diffie-Hellman group 20
- 1 hour
- Tunnel monitor on the Palo to ping the tunnel interface of the ASA constantly – this keeps the tunnel up and running.
- Since there is the “intrazone-default allow” policy on the Palo, you don’t need an explicit policy for allowing the VPN connection from “untrust to untrust”. If you have an own explicit deny any policy at the end of your policy set, you need an explicit allow policy for “ike” and “ipsec-esp”.
- No NAT between the internal networks (of course not ;))!
Palo Alto NGFW
Everything is done via the GUI:









Cisco ASA
You can do the configuration either via the ASDM “GUI”:








or through CLI commands (of course you have to change the IPv4 addresses, the PSK, the number of the VTI or the crypto ikev2 policy, etc.) Furthermore, the ACL is not listed:
interface Tunnel2 nameif pa ip address 10.1.227.2 255.255.255.252 tunnel source interface outside tunnel destination 193.24.227.9 tunnel mode ipsec ipv4 tunnel protection ipsec profile aes256gcm-sha512-dh20-3600s ! route pa 193.24.227.224 255.255.255.224 10.1.227.1 1 ! crypto ipsec ikev2 ipsec-proposal aes256gcm-sha512 protocol esp encryption aes-gcm-256 protocol esp integrity sha-512 crypto ipsec profile aes256gcm-sha512-dh20-3600s set ikev2 ipsec-proposal aes256gcm-sha512 set pfs group20 set security-association lifetime seconds 3600 crypto ikev2 policy 2 encryption aes-256 integrity sha512 group 20 prf sha512 lifetime seconds 28800 ! group-policy 193.24.227.9 internal group-policy 193.24.227.9 attributes vpn-tunnel-protocol ikev2 tunnel-group 193.24.227.9 type ipsec-l2l tunnel-group 193.24.227.9 general-attributes default-group-policy 193.24.227.9 tunnel-group 193.24.227.9 ipsec-attributes ikev2 remote-authentication pre-shared-key ThisIsThePreSharedKey ikev2 local-authentication pre-shared-key ThisIsThePreSharedKey
Monitoring
On the Palo you can see these information in the GUI:




Or you can use some of these CLI commands show vpn { ike-sa | ipsec-sa | gateway | tunnel | flow } :
weberjoh@pa> show vpn ike-sa gateway asa
There is no IKEv1 phase-1 SA found.
There is no IKEv1 phase-2 SA found.
IKEv2 SAs
Gateway ID Peer-Address Gateway Name Role SN Algorithm Established Expiration Xt Child ST
---------- ------------ ------------ ---- -- --------- ----------- ---------- -- ----- --
2 185.23.77.7 asa Init 90 PSK/DH20/A256/SHA512 Oct.07 14:23:04 Oct.07 22:23:04 0 1 Established
IKEv2 IPSec Child SAs
Gateway Name TnID Tunnel ID Parent Role SPI(in) SPI(out) MsgID ST
------------ ---- ------ -- ------ ---- ------- -------- ----- --
asa 4 asa 390604 90 Init D8EF49DF CF6D9FC7 00000793 Mature
Show IKEv2 SA: Total 2 gateways found. 1 ike sa found.
weberjoh@pa>
weberjoh@pa>
weberjoh@pa> show vpn ipsec-sa tunnel asa
GwID/client IP TnID Peer-Address Tunnel(Gateway) Algorithm SPI(in) SPI(out) life(Sec/KB) remain-time(Sec)
-------------- ---- ------------ --------------- --------- ------- -------- ------------ ----------------
2 4 185.23.77.7 asa(asa) ESP/G256/ D8EF49DF CF6D9FC7 3600/Unlimited 1185
Show IPSec SA: Total 1 tunnels found. 1 ipsec sa found.
weberjoh@pa>
weberjoh@pa>
weberjoh@pa> show vpn gateway name asa
GwID Name Peer-Address/ID Local Address/ID Protocol Proposals
---- ---- --------------- ---------------- -------- ---------
2 asa 185.23.77.7 193.24.227.9(ipaddr:193.24.227 IKEv2 [PSK][DH20][AES256][SHA512]28800-sec
IKEv2 cookie will be enabled if the number of half opened SA is over 500
IKEv2 max allowed half opened SA: 65535
weberjoh@pa>
weberjoh@pa>
weberjoh@pa> show vpn tunnel name asa
TnID Name Gateway Local Proxy IP Ptl:Port Remote Proxy IP Ptl:Port Proposals
---- ---- ------- -------------- -------- --------------- -------- ---------
4 asa asa 0.0.0.0/0 0:0 0.0.0.0/0 0:0 ESP tunl [DH20][AES256-GCM16][SHA512] 3600-sec 0-kb
Show IPSec tunnel config: Total 1 tunnels found.
weberjoh@pa>
weberjoh@pa>
weberjoh@pa> show vpn flow name asa
tunnel asa
id: 4
type: IPSec
gateway id: 2
local ip: 193.24.227.9
peer ip: 185.23.77.7
inner interface: tunnel.4
outer interface: ethernet1/1
state: active
session: 62916
tunnel mtu: 1432
soft lifetime: 3494
hard lifetime: 3600
lifetime remain: 1075 sec
lifesize remain: N/A
latest rekey: 2525 seconds ago
monitor: on
monitor status: up
monitor dest: 10.1.227.2
monitor interval: 3 seconds
monitor threshold: 5 probe losses
monitor bitmap: 11111
monitor packets sent: 318909
monitor packets recv: 318905
monitor packets seen: 0
monitor packets reply:0
en/decap context: 967
local spi: D8EF49DF
remote spi: CF6D9FC7
key type: auto key
protocol: ESP
auth algorithm: NULL
enc algorithm: AES256GCM16
traffic selector:
protocol: 0
local ip range: 0.0.0.0 - 255.255.255.255
local port range: 0 - 65535
remote ip range: 0.0.0.0 - 255.255.255.255
remote port range: 0 - 65535
anti replay check: yes
copy tos: no
enable gre encap: no
initiator: yes
authentication errors: 0
decryption errors: 0
inner packet warnings: 0
replay packets: 0
packets received
when lifetime expired:0
when lifesize expired:0
sending sequence: 1224
receive sequence: 1215
encap packets: 324665
decap packets: 324016
encap bytes: 38722120
decap bytes: 36924228
key acquire requests: 14
owner state: 0
owner cpuid: s1dp0
ownership: 1
On the ASA these are the GUI information. Note the proxy-IDs aka “Local Addr. / Subnet Mask / Protocol / Port” which is “0.0.0.0/0.0.0.0/0/0” which is absolutely correct, due to the usage of a route-based VPN. Nice!



And here are some CLI commands as well. Note that you have a valid static route to the other side, which is great!
asa# show crypto ikev2 sa detail
IKEv2 SAs:
Session-id:14, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote Status Role
1064907123 185.23.77.7/500 193.24.227.9/500 READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA512, DH Grp:20, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 28800/19548 sec
Session-id: 14
Status Description: Negotiation done
Local spi: 7717F9B4C00B4B1F Remote spi: 9C74DCB332A67F2C
Local id: 185.23.77.7
Remote id: 193.24.227.9
Local req mess id: 3 Remote req mess id: 3911
Local next mess id: 3 Remote next mess id: 3911
Local req queued: 3 Remote req queued: 3911
Local window: 1 Remote window: 1
DPD configured for 10 seconds, retry 2
NAT-T is not detected
IKEv2 Fragmentation Configured MTU: 576 bytes, Overhead: 28 bytes, Effective MTU: 548 bytes
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0x608b2209/0xe8a8c944
AH spi in/out: 0x0/0x0
CPI in/out: 0x0/0x0
Encr: AES-GCM, keysize: 256, esp_hmac: N/A
ah_hmac: None, comp: IPCOMP_NONE, mode tunnel
Parent SA Extended Status:
Delete in progress: FALSE
Marked for delete: FALSE
asa#
asa#
asa# show crypto ipsec sa peer 193.24.227.9 detail
peer address: 193.24.227.9
Crypto map tag: __vti-crypto-map-6-0-2, seq num: 65280, local addr: 185.23.77.7
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 193.24.227.9
#pkts encaps: 35910, #pkts encrypt: 35910, #pkts digest: 35910
#pkts decaps: 23421, #pkts decrypt: 23421, #pkts verify: 23421
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 35910, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#pkts no sa (send): 0, #pkts invalid sa (rcv): 0
#pkts encaps failed (send): 0, #pkts decaps failed (rcv): 0
#pkts invalid prot (rcv): 0, #pkts verify failed: 0
#pkts invalid identity (rcv): 0, #pkts invalid len (rcv): 3974389472
#pkts invalid pad (rcv): 0,
#pkts invalid ip version (send): 0, #pkts invalid ip version (rcv): 0
#pkts invalid len (send): 0, #pkts invalid len (rcv): 0
#pkts invalid ctx (send): 0, #pkts invalid ctx (rcv): 0
#pkts invalid ifc (send): 0, #pkts invalid ifc (rcv): 0
#pkts failed (send): 0, #pkts failed (rcv): 0
#pkts replay rollover (send): 0, #pkts replay rollover (rcv): 0
#pkts replay failed (rcv): 0
#pkts min mtu frag failed (send): 0, #pkts bad frag offset (rcv): 0
#pkts internal err (send): 0, #pkts internal err (rcv): 0
local crypto endpt.: 185.23.77.7/500, remote crypto endpt.: 193.24.227.9/500
path mtu 1500, ipsec overhead 55(36), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: E8A8C944
current inbound spi : 608B2209
inbound esp sas:
spi: 0x608B2209 (1619730953)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 20, IKEv2, VTI, }
slot: 0, conn_id: 41, crypto-map: __vti-crypto-map-6-0-2
sa timing: remaining key lifetime (kB/sec): (3962843/2426)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0xFFFFFFFF 0xFFFFFFFF
outbound esp sas:
spi: 0xE8A8C944 (3903375684)
SA State: active
transform: esp-aes-gcm-256 esp-null-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 20, IKEv2, VTI, }
slot: 0, conn_id: 41, crypto-map: __vti-crypto-map-6-0-2
sa timing: remaining key lifetime (kB/sec): (3916764/2426)
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
asa#
asa#
asa# show route static
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
Gateway of last resort is 185.23.77.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 185.23.77.1, outside
S 193.24.227.224 255.255.255.224 [1/0] via 10.1.227.1, pa
PS: Sorry for being legacy IP only this time. ;(
Photo by Mathew Schwartz on Unsplash.