
In the previous post, I released my Ultimate PCAP which includes every single pcap I had so far on my blog. But that’s not all: I have some packets in there that were not yet published up to now. That is, here are some more details about those (probably well-known) protocols. These are:
DNS Dynamic Update
(Not to be confused with DynDNS for your home router.) I updated three RRs (A, AAAA, PTR) to my authoritative DNS server. While my server is authoritative and within the global DNS tree for “ib-unsigned.weberdns.de”, it’s quite obviously not in the DNS tree for the IPv4 address block reserved for documentation (RFC 5737), 198.51.100.0/24. Hence I had to set the server manually.
weberjoh@nb15-lx:~$ nsupdate > update add newhost.ib-unsigned.weberdns.de. 300 A 198.51.100.42 > send > update add newhost.ib-unsigned.weberdns.de. 300 AAAA 2001:db8:0:1::42 > send > update add 42.100.51.198.in-addr.arpa. 60 PTR newhost.ib-unsigned.weberdns.de. > send couldn't get address for 'nobody.invalid': not found weberjoh@nb15-lx:~$ nsupdate > server ib1.weberdns.de > update add 42.100.51.198.in-addr.arpa. 60 PTR newhost.ib-unsigned.weberdns.de. > send > quit
This is what the updates look like in Wireshark:
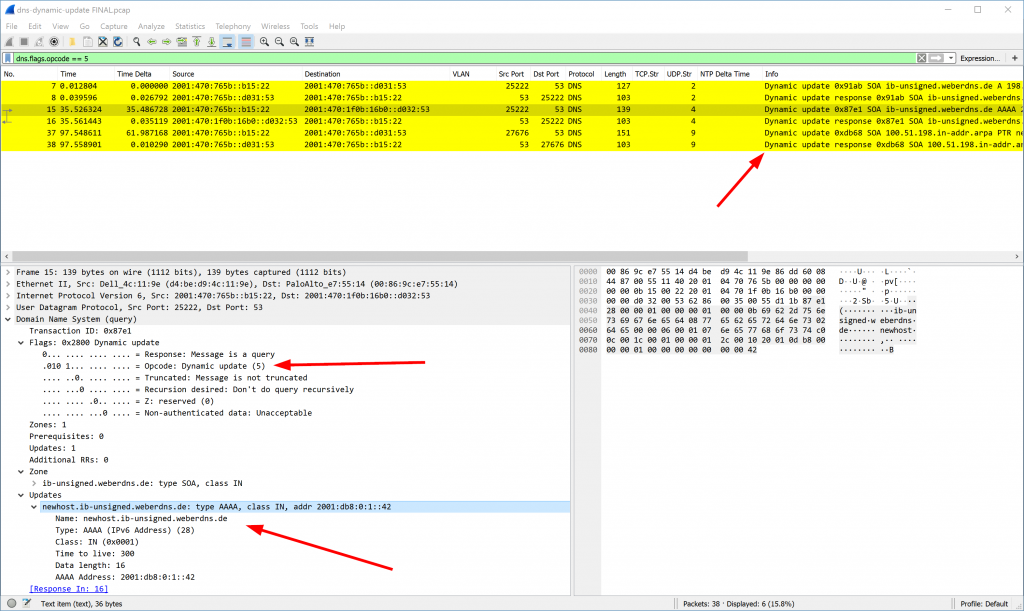
IPv6 Router Advertisement (RA) with RDNSS and DNSSL
Router advertisements with the recursive DNS server option and the DNS search list option (of course, along with the default prefix information). Also, note the delta time (red marked box, a custom column in Wireshark) as it varies randomly between 19-60 seconds since I manually configured those min and max values. (Due to RFC 4861, the min should be 0.33*max.)

DHCPv6 Prefix Delegation
Router to router conversation via DHCPv6-PD in which the downstream router asks for a prefix. In my case, it gets a /56 one:

Telnet
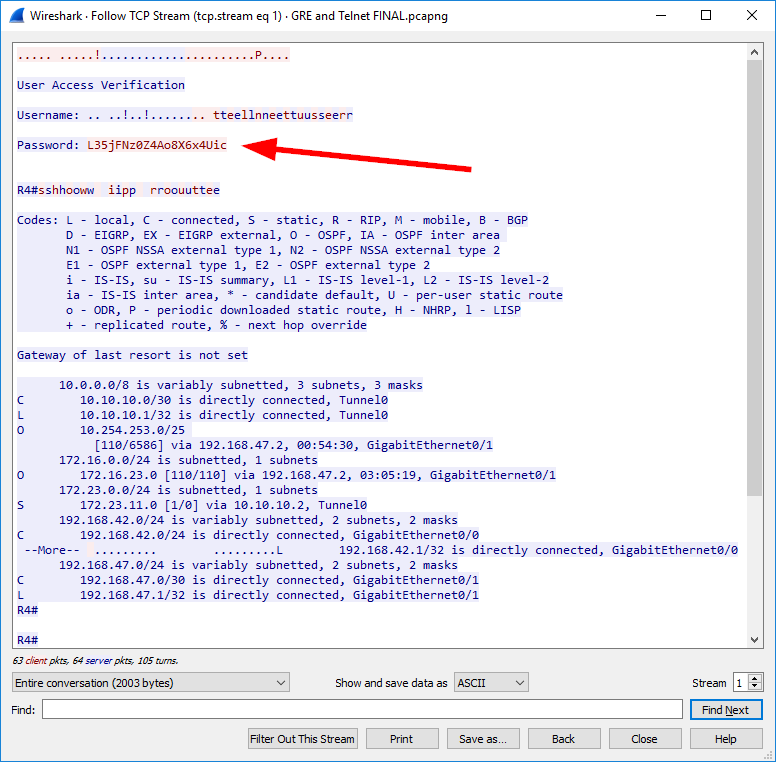
Uh, wait, what? Yes, it’s Telnet. For the sake of completeness. Not because I’m using it, but because it’s still alive. Follow TCP Stream and you can see everything, including the login password. Ouch. Welcome to 2020. ;)
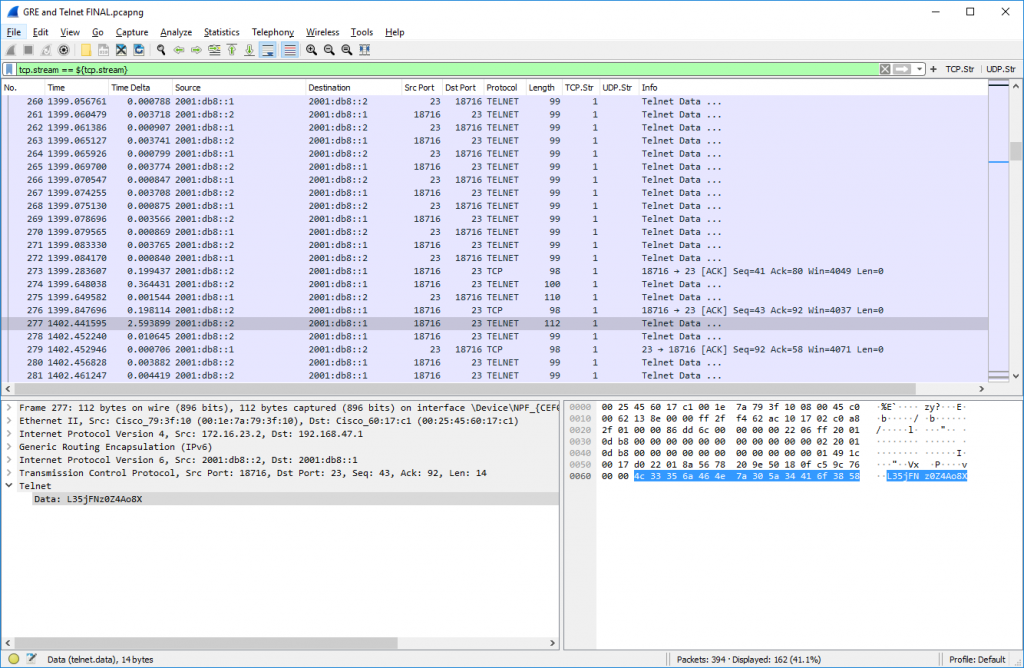
Generic Routing Encapsulation (GRE)
A tunneling protocol that is known from Cisco but used by other vendors as well such as Palo Alto Networks NGFW. In its basic usage, it is tunneling IP in IP. It is a layer 4 protocol with protocol number 47. (Not to be confused with TCP/UDP port numbers.) In my capture, I am using legacy IP tunnel endpoints while IPv6 and IPv4 were tunneled. You’ll find pings, traceroute and an SSH connection. Note that Wireshark displays the tunneled source/destination IP addresses (which is great!):
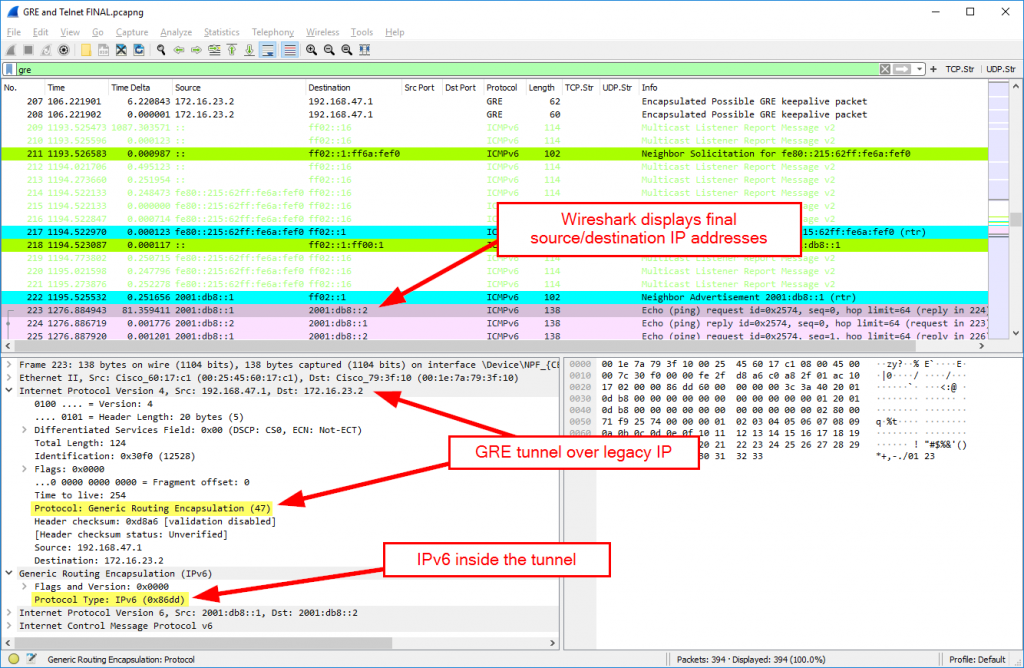
If configured, keepalives are sent from both sides. “When you enable keepalives on the tunnel endpoint of Router A, the router at every interval constructs the inner IP header. At the end of the header, the router also appends a GRE header with a Protocol Type (PT) of 0, and no other payload”, How GRE Keepalives Work:

NetFlow
Reporting metadata of IP flows to a flow collector. In my case, a Palo Alto Networks firewall sends NetFlow version 9 packets. Some data-templates are also found in the trace.

Blessings!